
Malware analysis and reverse engineering seem to be technical but it’s much easier than we think, Malware has become a major threat to organization and PC users across all over the world and we definitely need to know some basics of these analysis tools, so we can detect most of the sticky and dangerous threat easily before any great loss.
I know that antivirus programs do their job nicely but we also ready if in case of windows corruption because many of the time I have seen that many high severity threats easily block your antivirus if the antivirus is outdated or disable for some reason.
There are several types of malware analysis which greatly helpful for analysing your computer for any threats like static malware analysis, dynamic malware analysis, behavior malware analysis, reverse engineering analysis, network analysis, and for analysing and detecting threats we can use plenty of tools like PeStudio, Process Hacker, Process Monitor (ProcMon), Autoruns, Ghidra, Cuckoo Sandbox, Wireshark, etc.
Check out more here:
So, let’s get started
Malware Analysing Techniques
Static malware analysis
In this process of analysing the malware detector detect malware without malware running the code and this accomplished through two major techniques
Signature-based technique – in this technique the detector detects malware through malware pattern or binary code signature. Basically, it is used to confirm, at least get an idea whether the file or application being inspected is malicious or not
Heuristic-based technique – In this technique, the detector detects the threat by command and instruction not present in application or program.
These both analysis techniques you might be seen in an antivirus program mostly antivirus programs used signature and heuristics-based approach to detect malware.
Dynamic malware analysis
This process of analysing involves running the malware sample and observing its behavior. This is carried out in a closed, isolated virtual environment or Sandbox so that the malware sample can be studied and not affecting the other system.
Hybrid analysis
In this analysis, both static and dynamic techniques involve file fingerprint, reverse engineering, packer detection, etc. then studied its behavior.
Network traffic analysis
Analysing network traffic that flows from routers would allow you to identify suspicious behavior of any kind of script and malware through any medium. Network analysing a term used IOC (Indication of compromise) which include IP Address, Domain name, User-Agent, Hostname, File Hashes, Specific term.
Now, we know about some basics of these different types of analysis techniques let’s talk about the malware analysing tools and how does it work.
Dynamic Analysis Tools
Process Explorer
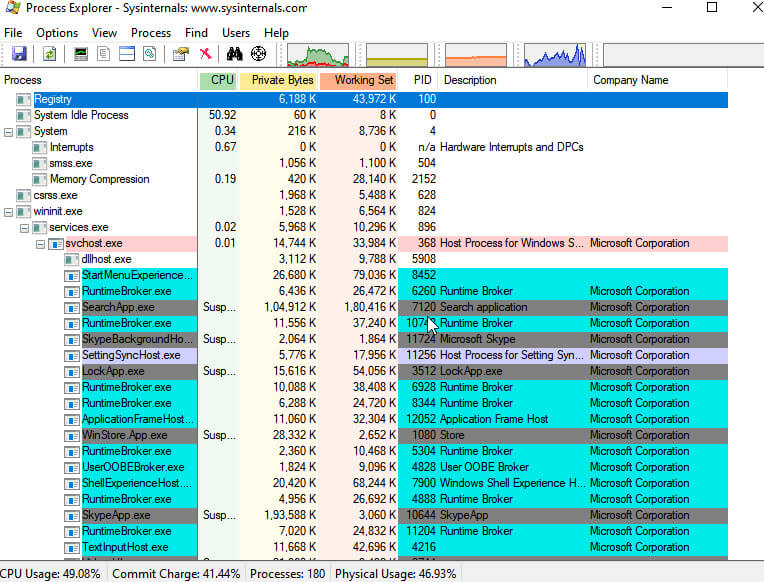
Process Explorer is part of Sysinternals which is now maintained by Microsoft, this is an excellent tool to get information of any system at a glance very quickly, it shows all the process running in the system currently with description and company name and it also has a plugin of Virus Total so you can see which process behavior is clean or not.
You can go to Option and Submit your samples or executables so that get scan them.
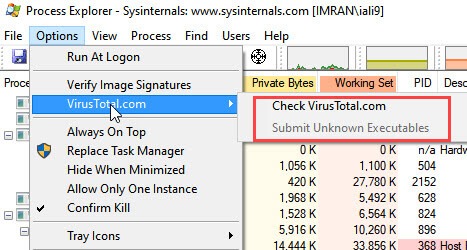
You can also look for process specifically by double click on it and this will tell you a lot more detail like Path, Command line, Directories, etc.
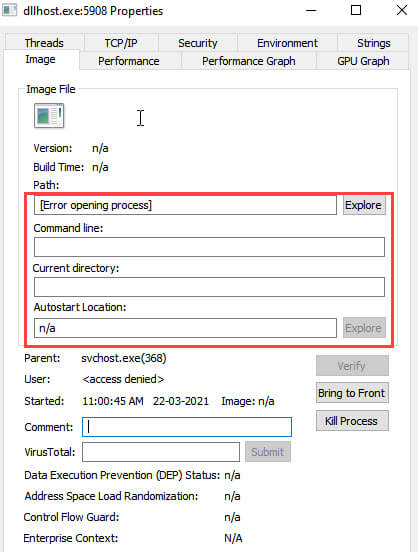
Now, look at the detail of Performance, Security, Threads, and Strings so you can match for any suspicious application.
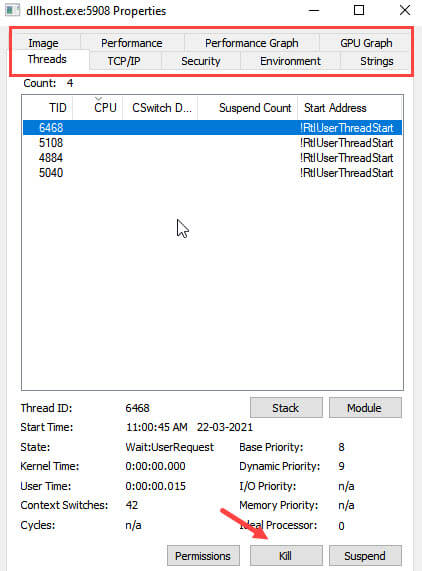
You can also Kill, Suspend or Restart any process like task manager.
Process hacker
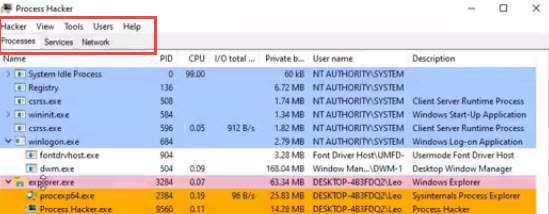
Process Hacker is a quick alternative to Process Explorer with same functionality. In this tool you can also look for modules, statistics, performance, threads like process explorer I only miss the virus total plugin in this tool but overall it is a great tool for beginners.
Autoruns
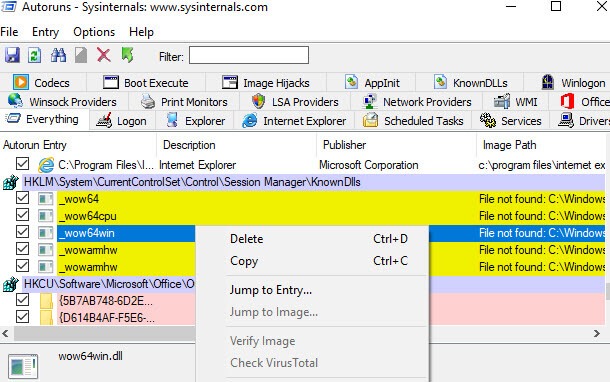
Autoruns is one of the simplest tool this is again part of Sysinternals and as the name suggest this tool shows you every process and program run in the background of the system and it has also virus total plugin so you can quickly check whether a process or program is malware or not.
It has many useful features and much more extensive than the start-up list of task manager so I definitely recommend having this in your tool kit.
Process Monitor
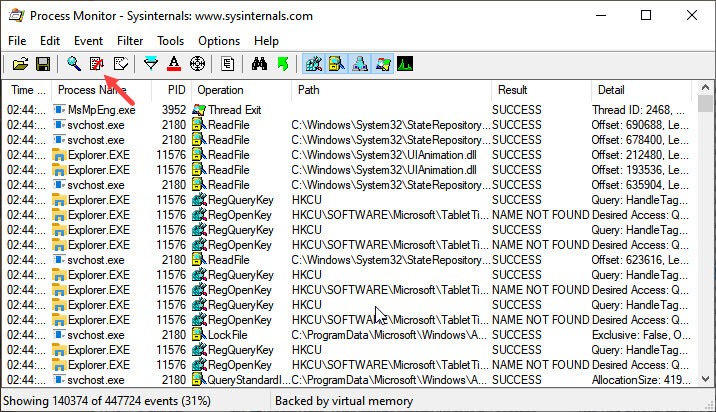
ProcessMonitor is one of the best and advance tool for malware inspection as the name suggest it shows all your system process and see exactly what they’re doing not in the term of CPU usage or what they running but all the instruction passing through the operating system.
If you turn Auto-scroll you can see a lot going on even if you’re not doing anything
You can use Filters in process monitor to include or exclude any kind of specific entry.
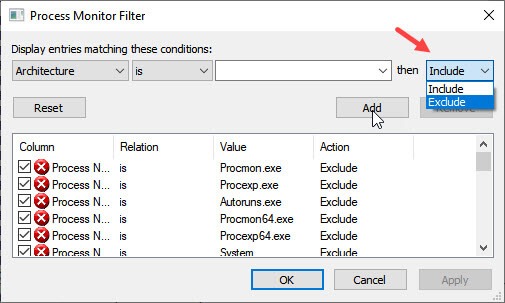
If you know what you looking for then this is exactly tools you need.
Regshot
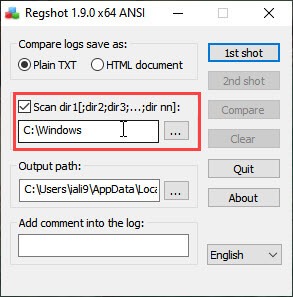
Regshot uses to take a snapshot before or after a malware infection and also scan every directory and path you specify if you are run ransomware for any kind of dynamic testing you can take a shot of the registry before running and take a shot after running to differentiate the changes in the registry and directories.
It is an easy-to-use tool little bit difficult to read log files but overall a great tool.
OllyDbg
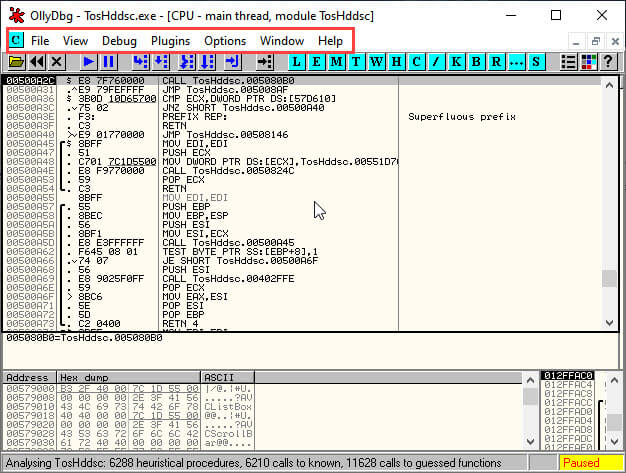
Ollydebugger is most advanced dissembler tool and not for all, this tool specially used by programmers and application builders and also used for analysing specific programs through different coding’s, and this tool also used for reverse engineering of applications.
It is extremely useful for going through specific program codes and tried to understand the program in detail.
Static Analysis Tools
PeStudio
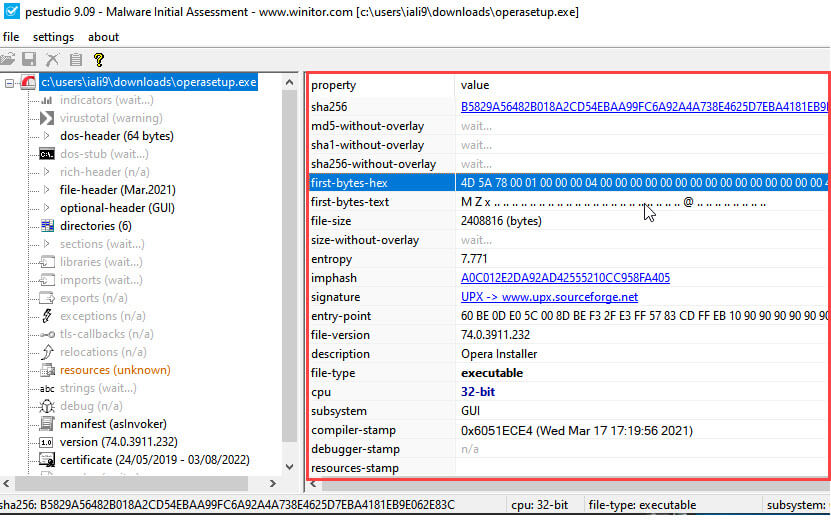
PeStudio is a static analysing tool if you’re a beginner and if you look for any piece of malware statically then this tool is great for you. You need to drag and drop any executable to this tool and it will tell you everything about it like hashes, signature hashes, file version, description, file type, etc. it has also virus total scan allows you to scan for malware.
dnSpy
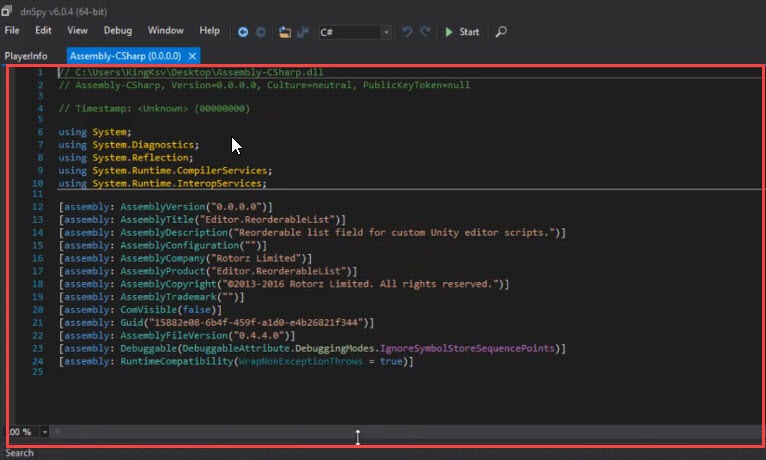
dnSpy is a decompiler if you are familiar with programming then you know that it is reverse of compiler means that this tool converts low-level code to high-level language. You can drag and drop executable to PeStudio and get the source code and put the source code in this tool to read into it and look at different section of program
this is a great tool but obviously, you need to familiar with coding to understand this tool
Ghidra
Ghidra is a reverse engineering (SRE) software framework developed by NSA’s Research Directorate for NSA’s cybersecurity mission. It helps you to analyse malicious code and malware which gives cybersecurity professionals a better understanding of potential vulnerabilities and suspicious behavior in their networks and systems.
This tool helps you to disassemble a program and read assembly codes of program but again this tool used by programmers and you need to familiar with assembly codes and other programming codes and the best alternative of this tool is IDA Pro but Ghidra is free tool and IDA pro is paid tool.
Cuckoo Sandbox
Cuckoo Sandbox is free open source software that automated the task of analysing and understanding any malicious file and programs behavior under Windows, macOS, Linux, and Android. It is ideal for an Enterprise environment, can be used to assist a malware analyst and gather IOC’s, it Performs advanced memory analysis of the infected virtualized system through Volatility as well as on a process memory granularity using YARA.
This tool needs some additional packages to install first.
Network Analysis Tool
Wireshark
Wireshark is a popular tool for analysing network traffic and there are lots of feature to detecting malware usually, programmers use OIC to looking for what infected files, hashes, URL, IP address, Hostname, or Mac address of the infected machine
You may also like: –
- How to password protect folders in windows
- How to fix Blu screen of death (BSOD)
- Best software for Windows
Conclusion
Analysing and inspection of a system is not a big deal, we have numbers of tool which some of easy to use and to run some tools we need to know about some coding and programming language, anyway I tried to explain all these tools which are used in analysing malware or any vulnerabilities in windows or any network.
If you like this post don’t forget to share
